

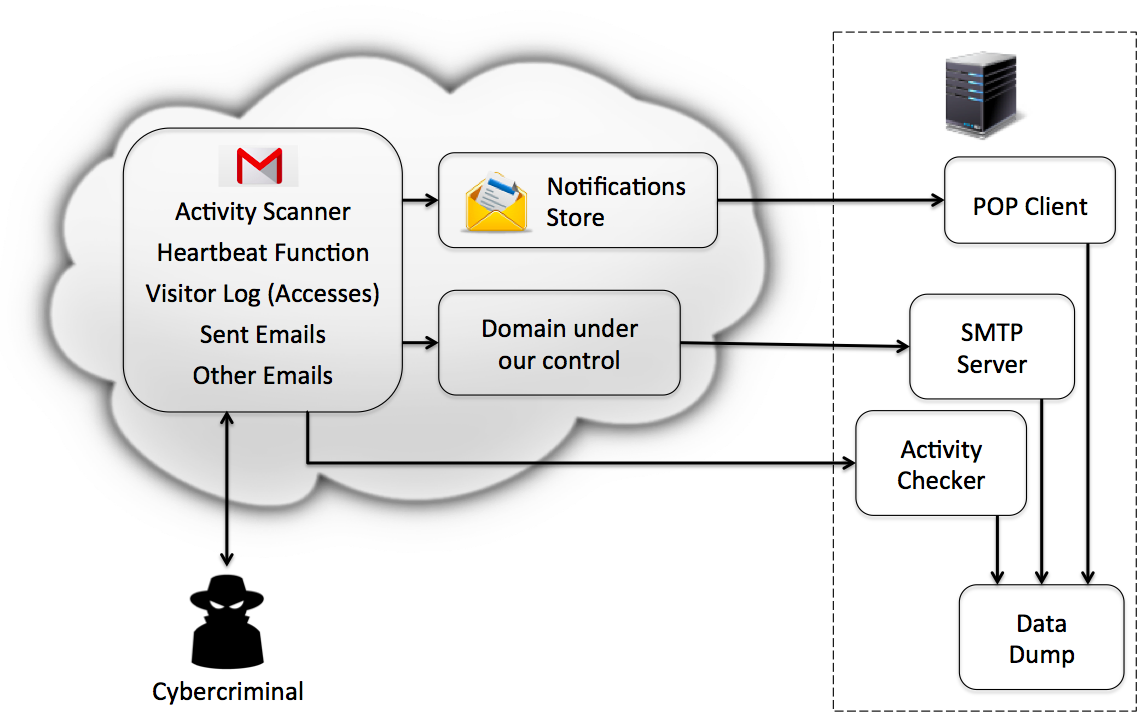
Cybercriminals compromise user credentials and later access their accounts with the goal of performing additional activities (e.g., sending spam or harvesting sensitive information). In this project we set up believable fake accounts (honeypots) and have criminals access them, with the goal of better understanding their modus operandi and their motivations.
Jeremiah Onaolapo, Enrico Mariconti, and Gianluca Stringhini.
IMC, 2016.
Dario Adriano Bermudez Villalva, Jeremiah Onaolapo, Mirco Musolesi, and Gianluca Stringhini.
Journal of Crime Science, 2018.
Martin Lazarov, Jeremiah Onaolapo, and Gianluca Stringhini.
CSET, 2016.
Emeric Bernard-Jones, Jeremiah Onaolapo, and Gianluca Stringhini.
CYBERSAFETY, 2016.